So it started with an idea. How cool would it be to get everybody to install a QR code reader and read temporary tattoos off each other? Anyway, at Shmoocon I walked around with a bag of QR temporary tattoos much to the delight and chagrin of the hackers assembled therein.
The howto:
#1 Get a barcode generator. I use zint, it’s my favorite tool for generation. For those of you on Ubuntu or Debian, I have packages built for you. And give the zint guys some money while you’re at it, they use the funds to buy standards and make zint work with every symbology known to mankind.
#2 Get a layout program. I use Inkscape. Key here is that it has to be able to import .svg files and be able to flip images horizontally.
#3 Get printable temporary tattoo paper. It’s not really cheap, but I found kits on tattoofun.com. The kit consists of waterslide temporary tattoo paper, adhesive sheets, and an instruction sheet.
#4 Make .svg Barcodes! I load up zint and toss some text at it, then use the QR symbology. Some examples:
- sms:7035551234 body:Greetz from teh Internetz
- MATMSG: TO:shredder@guerilla-ciso.com; SUB:Test; BODY:This is a test. Please reply if received.;;
- MECARD:N:Wizzleteague, Stinky;ADR:1234 Main St, Arlington, VA 22202;TEL:+17035551234;EMAIL:shredder@guerilla-ciso.com;;
- Hi, I’m Quine. I haz a RAGE! https://twitter.com/quine
- I went to Shmoo and all I got was the flu
- BTW, if you want to pay me to make QR tattoos for promotion events, drop me an email.
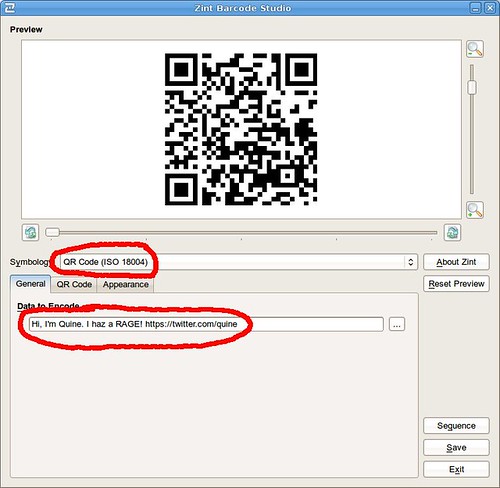
#4.5 Add in QR error correction. The more error correction you use, the more data in the barcode so the smaller the blocks are. However, some error correction compensates for distortion and glare. IIUC, Zint automagically adds in 20% error correction. I’m not sure what the magic number here is because it depends on the size of the printed barcodes.

#5 Export barcode from zint. SVG is awesome to save as because you can scale the barcodes up as much as you want and they won’t get all pixelated-looking. You can grab a ton of the barcodes I made here.

#6 Import barcode into inkscape. File=>Import then select the .svg file you want. Since the barcodes are svg, you can scale them awesomely. For mine, I set up guidelines so I could lay out rows proportionately. Be sure to lock the object proportions or you’ll get hideously warped QR monstrosities that nothing can read. You can grab my sheet of barcodes here.

#7 Make “The Big Flip” and print. Inkscape-specific: Edit=>Select All followed by Object=>Flip Horizontal. Then print the page on the glossy side of the slide water paper.
#8 Add the sticky. It’s a bit like laminating a map only the adhesive is way more forgiving. Poke some pin-holes in the adhesive sheet and smooth out all the bubbles.
#9 Cut, peel, stick, wet, pull, read, lol. You can get a reader here, but the important bits: iTunes Store: Barcodes. Android: Barcode Scanner.
Lessons Learned:
Laser barcode scanners don’t work because the film is reflective. Photo-based barcode scanners (ie, most mobile scanners) work pretty well.
You have to make the barcodes bigger than I did. Mine were .75x.75 inches and due to the glare on the paper and some distortion due to putting them on skin, they were hard to read. I think maybe 2×2 inches are optimum.
Hackers don’t like informational urls in their tattoos: “I got an add for ZXing, this sucks”. I think random goofy phrases and skin pwnage would work better than informational urls.
Some people (Quine) weren’t happy with a grab-bag random url and needed their own custom witty saying. I felt the rage, it has now been fixed.
You can’t read the barcodes until they’re on the skin because of the horizontal flip. Before you do the flip, print out the barcodes on regular paper. You can read these easily enough. Then flip the finished barcode sheet over after you’ve printed it and you can match up the barcode with the non-flipped sheet. Even better if you use your computer monitor as a lightbox.

Similar Posts:
 No Comments »
No Comments » Posts RSS
Posts RSS